Physical Address:
A34-Köshe, 17-Üi,
Astana, Qazaqstan
Physical Address:
A34-Köshe, 17-Üi,
Astana, Qazaqstan
We have 2 or mutiple entities with their own different LAN networks and different ISPs to join internet, but only via single router as gateway.
In our example we use Mikrotik router and switch, Please see below network topology for the desgin.
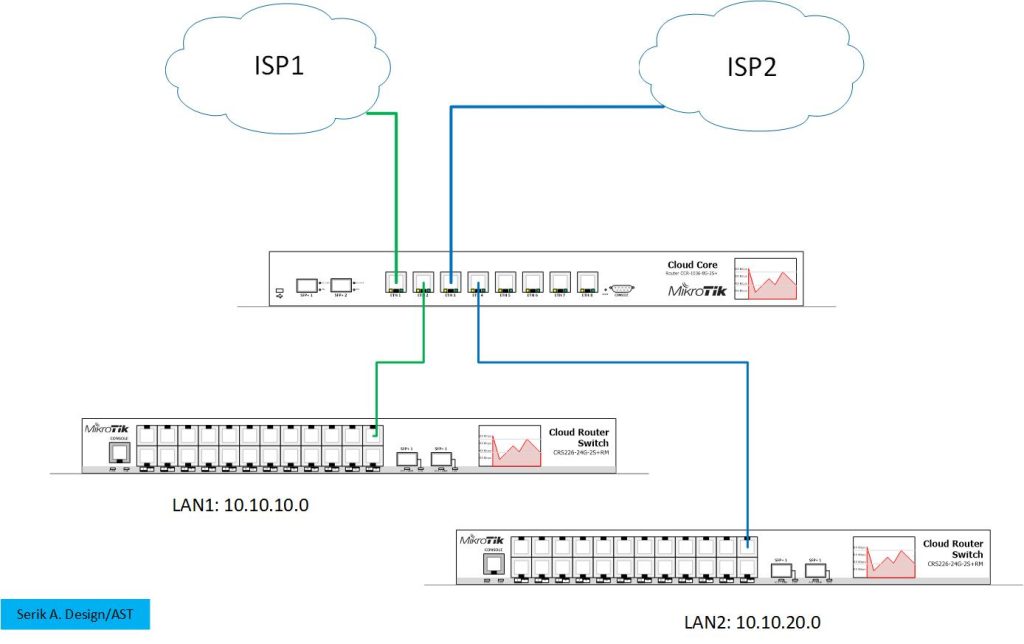
All configuration will be done on the mikrotik router, and we only use 2 ISP access, but you can extend the configuratiuon to multiple ISP access, eg 3 or more.
Set interfaces on the router and asign names on the ports we use:
/interface ethernet
set [ find default-name=ether1 ] name=ETH1-ISP1
set [ find default-name=ether2 ] name=ETH2-LAN1
set [ find default-name=ether3 ] name=ETH3-ISP2
set [ find default-name=ether4 ] name=ETH4-LAN2
/interface list
add name=LAN1
add name=ISP1
add name=LAN2
add name=ISP2
Add IP Pools and it’s IP address ranges:
/ip pool
add name=LAN1-Pool ranges=10.10.10.2-10.10.10.254
add name=LAN2-Pool ranges=10.10.20.2-10.10.20.254Configure DHCP server for LAN clients:
/ip dhcp-server
add address-pool=LAN1-Pool disabled=no interface=ETH2-LAN1 lease-time=5d \
name=LAN1-DHCP
add address-pool=LAN2-Pool disabled=no interface=ETH4-LAN2 lease-time=5d \
name=LAN2-DHCP
/interface list member
add interface=ETH1-ISP1 list=ISP1
add interface=ETH2-LAN1 list=LAN1
add interface=ETH3-ISP2 list=ISP2
add interface=ETH4-LAN2 list=LAN2
/ip address
add address=10.10.10.1/24 interface=ETH2-LAN1 network=10.10.10.0
add address=10.10.20.1/24 interface=ETH4-LAN2 network=10.10.20.0
/ip dhcp-client
add disabled=no interface=ETH1-ISP1
add disabled=no interface=ETH3-ISP2
/ip dhcp-server network
add address=10.10.10.0/24 dns-server=8.8.8.8,8.8.4.4 gateway=10.10.10.1
add address=10.10.20.0/24 dns-server=8.8.8.8,8.8.4.4 gateway=10.10.20.1Add DNS configuration:
/ip dns
set servers=8.8.8.8,8.8.4.4Most importent step is to setup firewall on the router:
/ip firewall address-list
add address=0.0.0.0/8 comment="Self-Identification [RFC 3330]" list=Bogons
add address=10.0.0.0/8 comment="Private[RFC 1918] - CLASS A # Check if you nee\
d this subnet before enable it" list=Bogons
add address=127.0.0.0/8 comment="Loopback [RFC 3330]" list=Bogons
add address=169.254.0.0/16 comment="Link Local [RFC 3330]" list=Bogons
add address=172.16.0.0/12 comment="Private[RFC 1918] - CLASS B # Check if you \
need this subnet before enable it" list=Bogons
add address=192.0.2.0/24 comment="Reserved - IANA - TestNet1" list=Bogons
add address=192.88.99.0/24 comment="6to4 Relay Anycast [RFC 3068]" list=\
Bogons
add address=198.18.0.0/15 comment="NIDB Testing" list=Bogons
add address=198.51.100.0/24 comment="Reserved - IANA - TestNet2" list=Bogons
add address=203.0.113.0/24 comment="Reserved - IANA - TestNet3" list=Bogons
add address=224.0.0.0/4 comment=\
"MC, Class D, IANA # Check if you need this subnet before enable it" \
list=Bogons
/ip firewall filter
add action=accept chain=forward comment="defconf: accept established,related" \
connection-state=established,related
add action=drop chain=forward comment="defconf: drop invalid" \
connection-state=invalid
add action=accept chain=input port=69 protocol=udp
add action=accept chain=forward port=69 protocol=udp
add action=drop chain=forward comment=\
"defconf: drop all from WAN not DSTNATed" connection-nat-state=!dstnat \
connection-state=new in-interface=ETH1-ISP1
add action=drop chain=forward connection-nat-state=!dstnat connection-state=\
new in-interface=ETH3-ISP2
add action=drop chain=forward comment="Drop to bogon list" dst-address-list=\
Bogons
add action=accept chain=input protocol=icmp
add action=accept chain=input connection-state=established
add action=accept chain=input connection-state=related
add action=drop chain=input in-interface=ETH1-ISP1
add action=drop chain=input in-interface=ETH3-ISP2
/ip firewall mangle
add action=mark-routing chain=prerouting comment="LAN1 to ISP1" \
new-routing-mark=LAN1-to-ISP1 passthrough=yes src-address=10.10.10.0/24
add action=mark-routing chain=prerouting comment="LAN2 to ISP2" \
new-routing-mark=LAN2-to-ISP2 passthrough=yes src-address=10.10.20.0/24
/ip firewall nat
add action=masquerade chain=srcnat out-interface=ETH1-ISP1
add action=masquerade chain=srcnat out-interface=ETH3-ISP2
Last step we need to setup the IP routing to let the LAN side clients to find out their own outbound gateway:
/ip route
add distance=1 gateway=192.168.1.1 routing-mark=LAN1-to-ISP1
//192.168.1.1 is ISP1 address
add distance=1 gateway=192.168.2.1 routing-mark=LAN2-to-ISP2
//192.168.2.1 is ISP2 address
/system clock
set time-zone-name=Asia/Almaty